Product Description
What is HI-TAM?
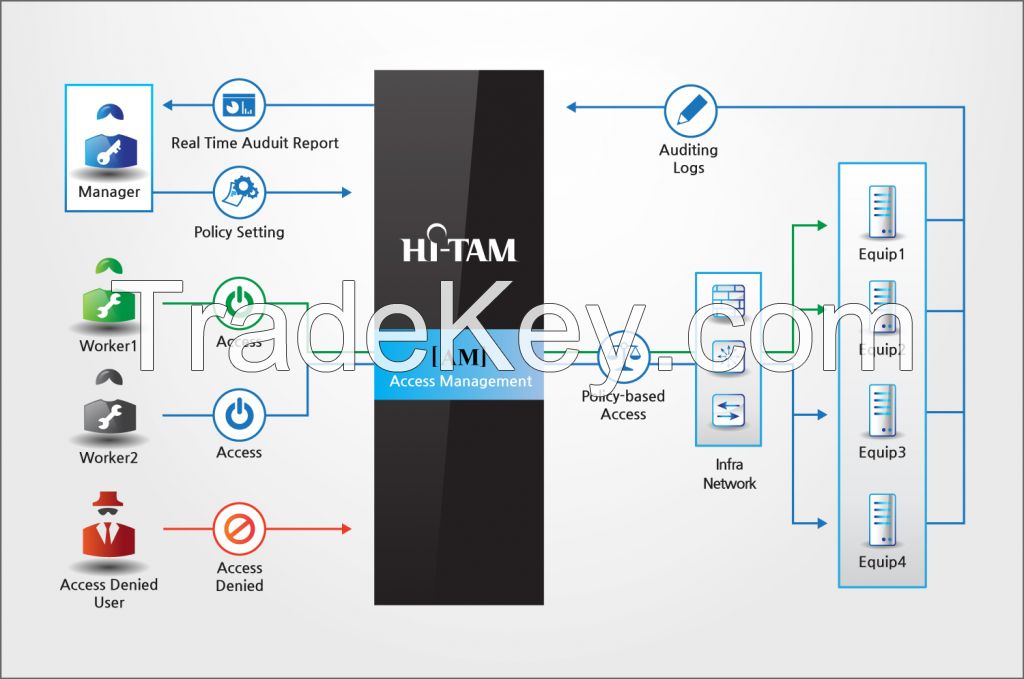
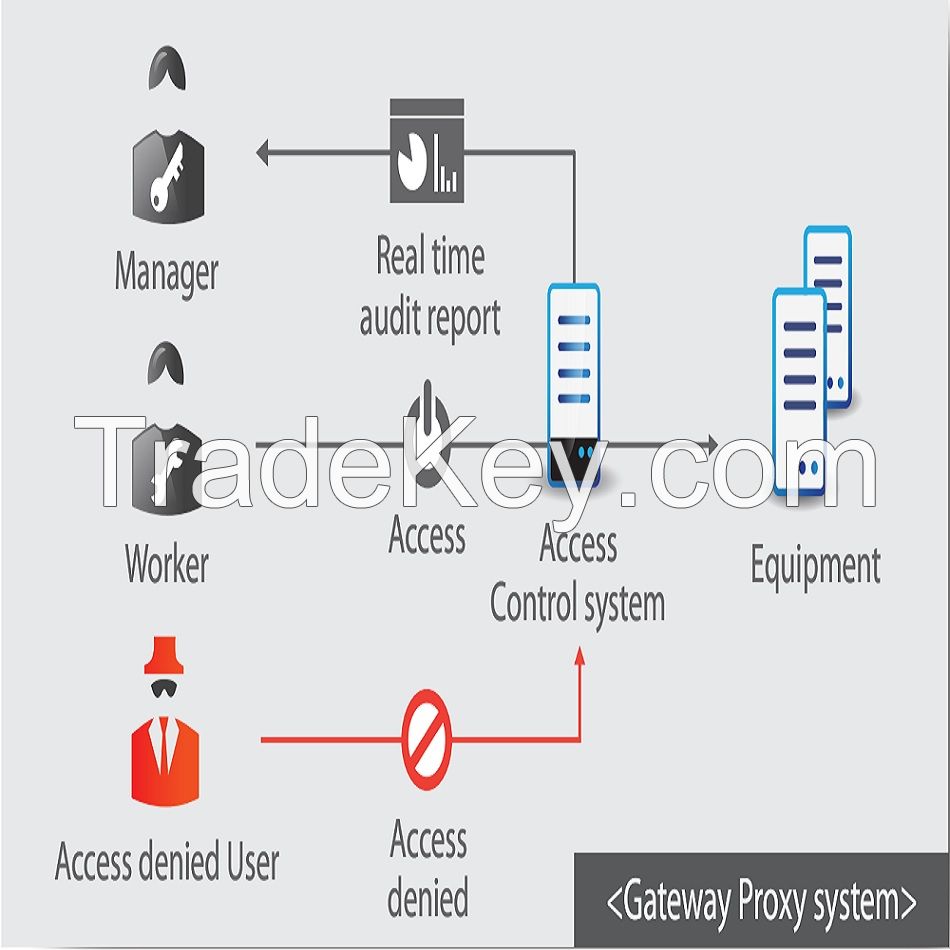
HI-TAM is Access Management solution of HI-WARE. HI-TAM controls
and manages remote access of IT system like network, server, etc.,
sets prohibited command to prevent misuse by user, monitors users
session on real time, and creates as audit logs.
HI-TAM can strengthen security by preventing unnecessary access and
human errors in advance, secure transparency in details of works
through audit log, and quickly solve system failure.
In case of using HI-TAM and HI-TIM (IM Solution) together, it will
enhance IT infrastructure security and work efficiency level by
integrating and managing both identity and access.
Features
Access Control
- Controlling each user/user group/account
- Centrally controlling access authority
- Default provide : Access IP, Access MAC, Access time
- Optional : 2(two) Factor certi¬cation
- Controlling each protocol (Telnet, SSH, SFTP, rlogin,
Windows Terminal Service, etc.)
- Unifying all remote accesses
- Distributing access authority according to the relevant
policy
- Access control alarm and access blocking
Command Control
- Setting authority to control command with various
conditions like each group/equipment, etc.
- Giving a warning when ting prohibited command and
then blocking sessions
- Requesting a managers approval via E-mail or SMS
- A managers approval is required for ting important
command
- Setting Telnet command as prohibited one and restricting
Leapfrog (CLI-based server)
- Applying prohibited command into White-list/Black-list
Log Record & Audit
- Storing all log records from the moment of access
- Supporting all forms including Text and Videos
- Compiling various statistics including each user/system /
command through search filter
- Sending one-to-one message to a worker when auditing logs
in real time
- Forcibly blocking sessions when a user commits illegal
acts
- Controlling speeds and Replaying screens when replaying
archive logs
Benefits
- Comply with regulations and policy
mandates
- Detailed access reports for troubleshooting, incident
investigation and simplification audits
- Ensures account passwords never reach
end-users(systems), preventing any misusage
- Efficiently control to prevent unwanted and malicious
access
- Enforce integrated policies to heterogeneous devices
and automate password management by workflow
| Country: |
South Korea |
| Model No: |
-
|
| FOB Price: |
( Negotiable ) (Negotiable)
Get Latest Price
|
| Place of Origin: |
- |
| Price for Minimum Order: |
- |
| Minimum Order Quantity: |
1 Unit |
| Packaging Detail: |
- |
| Delivery Time: |
- |
| Supplying Ability: |
- |
| Payment Type: |
T/T |
| Product Group : |
- |